Evolving Information Security: Aligning Strategies for a Digital Future
As organizations accelerate their adoption of new technologies to enable remote work, enhance customer experiences, and drive business value, the information security landscape is evolving at an unprecedented pace. With each new system and digital process, the attack surface expands, and cyber threats become more sophisticated and impactful. In this environment, aligning your information security strategy with organizational goals and risks is not just prudent—it's essential for creating value and ensuring long-term resilience during the software development lifecycle.
Building a Business-Aligned Security Strategy in a Rapidly Changing World
By Francisco T. Avalos, MBA, PMP, CSPO
As organizations accelerate their adoption of new technologies to enable remote work, enhance customer experiences, and drive business value, the information security landscape is evolving at an unprecedented pace. With each new system and digital process, the attack surface expands, and cyber threats become more sophisticated and impactful. In this environment, aligning your information security strategy with organizational goals and risks is not just prudent—it's essential for creating value and ensuring long-term resilience.
The Challenge: Accelerating Change and Growing Threats:
Technological innovation is reshaping how businesses operate, with investments in digital transformation, cloud adoption, and automation.
Security threats are growing in both frequency and sophistication, targeting organizations of every size and sector.
Remote work and digital customer engagement introduce new vulnerabilities, requiring security leaders to rethink traditional approaches.
Proactive Project Management, integrating Security into SDLC:
Security leaders as well as project managers must move beyond reactive measures and adopt a proactive, business-aligned approach. This means:
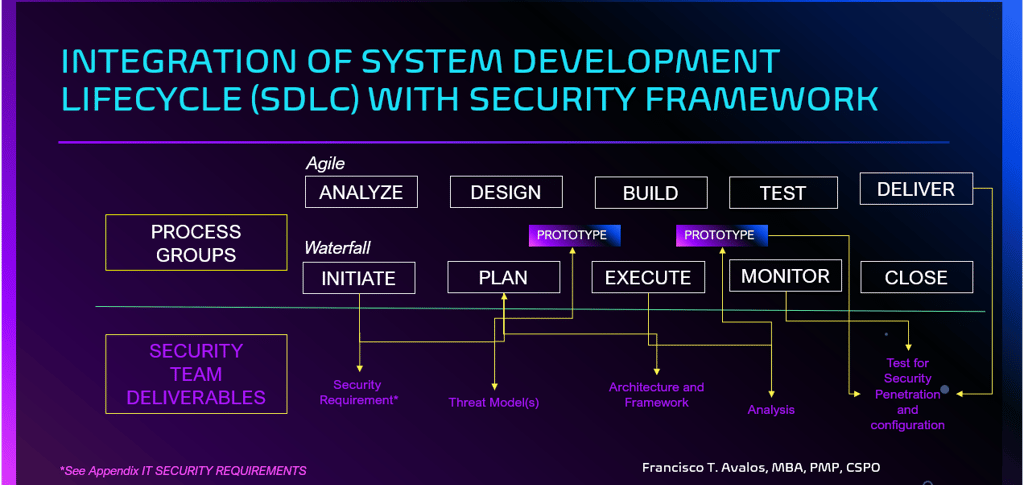
Integrating security considerations into every phase of the system development lifecycle (SDLC), from initial analysis to delivery (see Cyber-Security Framework)
Ensuring that security deliverables—such as requirements, threat models, architectural frameworks, and penetration tests—are embedded throughout the process.
Critical Insight: Beyond Frameworks:
While security frameworks provide valuable structure, they often fall short in guiding organizations on:
How to gather business requirements that drive security priorities.
Identifying and assessing organizational risks in the context of business goals.
Setting a realistic and practical target state for the security program.
Selecting the proper controls and conducting an accurate gap analysis.
The most successful security leaders are those who can balance investments in cyber resiliency with initiatives that support business growth and revenue generation.
Impact and Results: A Holistic Security Strategy:
To build a business-aligned, risk-aware, and holistic security strategy, organizations should enable the security team to participate in the various SDLC processes:
Gather Business Requirements
Engage stakeholders across the business to understand strategic priorities and operational needs.
Share and engage with the information security team for transparency.
Confirm the requirements with any risks associated with the company's security policies.
Assess Risks and Expectations
Evaluate internal and external risks, stakeholder expectations, and the organization's risk appetite.
Set meaningful, measurable targets for the security program.
Conduct a Comprehensive Gap Analysis
Identify where current security capabilities fall short of desired outcomes.
Use this analysis to pinpoint areas for improvement and resource allocation.
Build a Flexible Roadmap
Develop a security roadmap that is adaptable to changing business needs and emerging threats.
Ensure the roadmap includes clear milestones, accountability, and mechanisms for ongoing review and adjustment.
Conclusion:
In a world where technological change and cyber threats are accelerating, aligning your information security strategy with organizational goals and risks is key to creating business value and resilience. By engaging with information security at every phase of the project, for example, gathering business requirements, assessing risks, conducting gap analyses, and building flexible roadmaps, security leaders can position their organizations for success, protecting critical assets while enabling innovation and growth.
